Tragic events can happen in the blink of an eye. When there are preventions that could've resulted in different outcomes, we often wish we could turn back the clock and go for a redo! In hindsight, prevention may seem so effortless that the lack of effort to implement the precaution seems nonsensical. Common examples are seen in safety prevention efforts for very young children. It is a wee bit of effort to lock the knife drawer or the cabinet containing cleaning solutions. These small efforts in prevention have saved countless injuries in children. It is heartbreaking when a tragedy happens that could have been avoided.
A digital parallel to this example is the authentication of users. Trust in identity is a key element in the digital world. Static credentials can be stolen leaving ambiguity in the digital identity signing on to our systems. Proactive preventive actions can drive a deeper trust in the identity authenticating to your environment. Just as the simple installation of locks can prevent a tragedy for a family, advanced authentication methods can thwart a tragedy for an organization by driving a deeper trust in an identity prior to granting the identity access to enterprise-critical and data rich environments.
In many cases, a static password is all that is required for a person to become a trusted user. This is problematic for a number of reasons:
I'm glad to see that the 'The 2021 Data Breach Investigations Report' (DBIR) has separated past reports aggregation of brute force attack and stolen credentials accounting for over 80% of breaches.1 The separation of statistics now shows that stolen credentials account for over 80% and brute force hovers around 20%.2 This makes sense when we break this down. For a simplistic example, determining the correct combination for a password with a length of 8 and an available character set of 26 (all upper case letters) results in a number of combinations that is boggling to the human mind but straightforward for a machine to crack.
268=208,827,064,576 password combinations
Even as static passwords get more complex in length and available character sets result in exponential combinations where quantum computing would be required, brute force attack isn't the real threat. Mitigation controls will suspend an account long before all possible combinations can be attempted.
The threat lies in stolen credentials. The human factor continues to make the job of criminals easier as people tend to use easy passwords and reuse passwords from account to account. In 2018, it was estimated that we are each managing 200 passwords for various accounts and that number was expected to rise to 400 within 5 years3. With this high number of passwords we manage, it is human nature for most of us to reuse passwords or find a means to make password remembrance easier for ourselves. A review of nearly 300,000 passwords showed that less than half were unique and only 78 out of 200 of the most used-passwords of 2020 were new.4 This is concrete evidence that folks are reusing passwords and that they really are using passwords that no one should use from the 'Most used password list'. Passwords such as 'password' and 'qwerty' seem so easy, obvious, and ridiculous but folks, this is really occurring. Doh! Password sharing is a concern as well, especially as subscription services increase and people share the service and the cost.
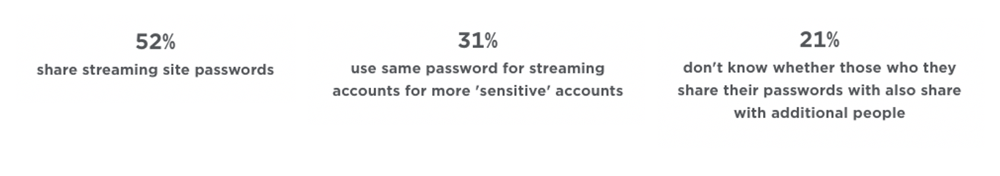 Table 1 Specops Password Safety Survey (5)
Table 1 Specops Password Safety Survey (5)
Password reuse doesn't only apply and remain segregated to personal sites. Once credentials are compromised from any site, those passwords lists can be tested in concert with identities anywhere to hack into an account including our organizations. Chances are great that a password posted in a stolen credential database has been used elsewhere and can be used to compromise your network and critical infrastructures when paired with an identity from your organization.
And here lies the reality - a quick ounce of prevention to implement changes in your environment can mitigate authentication risk substantially. Quick implementation of multifactor authentication fits into the Zero Trust Model to verify users upon entry to the mainframe environment and mitigate the risk of these problems. Adding additional factors to the authentication process requires input of a combination of known, possessed, or inherent factors making it much more difficult to gain access than when authentication is validated against an ID and static password alone. Multifactor authentication is a large return on investment to reduce risk. The average cost of a mega breach is estimated at $401M.6 The ounce of prevention via an advanced authentication solution on your mainframe may be already included in your licensing.
One may ask "Why do I need to implement multifactor authentication upon access to the mainframe if a user has authenticated with multiple factors into the network?" If you're asking this question, go back to the basics. Review layered security implemented in a series and the Zero Trust Model principle of "Never trust, always verify"! Access to your mainframe likely opens the door to the infrastructure enabling critical business processes and the platform storing high value transactional data. With a Zero Trust Model implementation, authentication occurs at the network boundary and again at the mainframe boundary. The whole reason for layered security in a series is for a succession of validations so compromises at any step can be mitigated or identified. Contrast this to the perimeter security approach - the one that brought us Solarwinds and Colonial Pipeline - that trust every user once validated which is no longer sufficient today.
Steps to take:
If you cannot move to multifactor in your mainframe environment at this very moment, at a bare minimum, review other controls:
Call for progress: World Password Day is May 5th, 2022. Challenge yourself and your organization to implement advanced authentication pervasively throughout your organization, inclusive of mainframe before the next World Password Day. Celebrate World Password Day 2022 knowing your organization is validating stronger credentials during authentication prior to trusting identities in your mainframe environment. Multifactor is a key initiative staving off many risks with static passwords, a common theme in compliance frameworks and regulatory controls, and should be looked into in the basic stages of Zero Trust assessment and implementation.
1. Verizon Data Breach Investigations Report 2020
2. Verizon Data Breach Investigations Report 2021
3. How many passwords can you remember? Get ready to remember more, TechXplore
4. Shibu, Sherin. 2020's Most Common Passwords are Laughably Insecure. 2020, November 18; Available from pcmag.com: https://au.pcmag.com/security/83948/2020s-most-common-passwords-are-laughably-insecure
5. Password security reveals accounts are at risk, Specops https://specopssoft.com/blog/password-security-survey-reveals-accounts-at-risk/?utm_source=Infosecurity&utm_medium=blog&utm_campaign=Infosecurity%20Magazine%20blog
6. Cost of a Data Breach Report, IBM Security
 Copyright © 2005-2025 Broadcom. All Rights Reserved. The term “Broadcom” refers to Broadcom Inc. and/or its subsidiaries.
Copyright © 2005-2025 Broadcom. All Rights Reserved. The term “Broadcom” refers to Broadcom Inc. and/or its subsidiaries.
Comments