In the ever evolving landscape of cybersecurity and system administration, decision makers are constantly re-evaluating their strategies to ensure efficiency, compliance, and overall robustness in safeguarding resources and data. One area of particular attention in this journey has been the method of user access control.
From multinational corporations to emerging businesses, ACF2 has been the bedrock upon which organizations have built their security frameworks, ensuring that their data remains inviolable amidst a constantly changing cyber threat landscape. Its enduring relevance, even in today's modern and complex digital age, speaks volumes about its robust architecture, adaptability, and the vision of its creators. As we delve deeper into the intricacies of user access control within ACF2, we must acknowledge the monumental role this system has played in shaping the security paradigms of the business world.
Traditionally, the UID string has been a staple in ACF2, serving as a unique identifier coupled with permissions to determine user access. While it has been possible to implement a role-based approach using the UID string, it hasn't been without its challenges.
Over the years, professionals navigating this space have voiced concerns regarding the UID string's complexity. While it offers granularity and can indeed be crafted to reflect roles, deciphering its intricacies and explaining them, especially to non-technical stakeholders, often becomes a daunting task. Further complicating matters is the concept of multi-value processing in ACF2. Though intended to provide flexibility in access control, its less-than-friendly nature often leaves administrators in a bind.
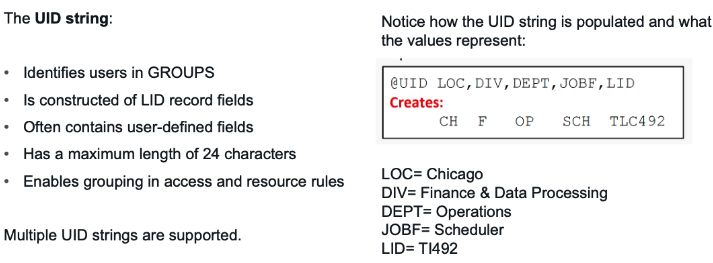
Another pivotal aspect influencing the thought process around UID strings and role-based access control (RBAC) is the regulatory environment. With several regulations now mandating a role-based approach, organizations are feeling the pressure. Explaining the nuances of the UID string to regulatory bodies and auditors is neither simple nor straightforward. For many, the shift to a more recognizable and standardized RBAC system seems like a logical step to alleviate these challenges.
However, the narrative isn't one-sided. Organizations that have judiciously crafted their UID strings—basing them on clear criteria such as site department, job functions, or specific applications—might find their system efficient and see little reason to transition to RBAC. Their UID strings, in essence, already mirror a role-based setup and serve their needs effectively.
On the other hand, sites that haven't been as meticulous in their UID string configuration, perhaps due to historical reasons or oversight, are prime candidates for considering ACF2 Roles. The benefits of clarity, standardization, and easier manageability that Roles bring can be particularly enticing for them.
Adding another layer to this discourse is the scenario where sites operate with multiple External Security Managers (ESMs). In environments where some logical partitions (lpars) are secured by other ESMs that already use Groups or Roles, the inconsistency introduced by ACF2's UID strings can be a genuine concern. For such sites, moving from the UID string in ACF2 to Roles becomes not just a matter of convenience, but also of consistency and streamlined security management across the board.
On one hand, the UID String, with its granular approach and unique identifiers, offers unparalleled specificity in user access controls, ensuring each individual is distinctly represented. On the other, the Role-based model introduces clarity, simplicity, and an intuitive structure that aligns with modern regulatory requirements and enterprise hierarchies. Both paradigms come with their respective merits, shaped by decades of real-world application and evolution.
The RBAC model, often seen as the modern response to access challenges, offers an intuitive structure. It aligns more naturally with enterprise hierarchies, providing a streamlined way of representing access rights based on roles within an organization. As regulatory pressures mount, and the need for clarity in access controls becomes paramount, the appeal of this model grows. It's a framework that speaks the language of today, making it more digestible for both administrators and external stakeholders.
But as with all transitions, the shift from UID Strings to Role-based models poses its questions. Where does one start? How can existing systems be seamlessly migrated without disrupting the current workflows? And more fundamentally, when is the right time to make the move?
Interestingly, the answer doesn't lie in a one-size-fits-all solution. Organizations that have masterfully crafted their UID strings, reflecting clear criteria and well-thought-out access patterns, may find little incentive to shift. Conversely, enterprises grappling with the complexities of their UID strings, or those operating in multi-ESM environments, might find the allure of RBAC too compelling to ignore.
Data owners become crucial stakeholders, ensuring that the segmentation and subsequent role allocation are reflective of actual access needs, thereby supporting security, compliance, and operational efficiency during and after the transition to a role-based access model in ACF2.
It’s clear that the journey through mainframe security, especially in the context of ACF2, is both fascinating and multifaceted. The choices made in user access control strategies can significantly influence an organization's security posture, operational efficiency, and regulatory compliance. While we've dissected the nuances and pondered the best paths forward, the ultimate decisions rest with the organizations themselves, informed by their unique histories, present challenges, and visions for the future.
Imagine overseeing an ACF2 system with a staggering 60,000 users. For over two decades, access grouping within this system has been orchestrated using UID Strings. With such an extensive history, it's plausible that many users possess more permissions than they genuinely require.
This excess can stem from numerous reasons: Individuals might have shifted through different positions in the company, accumulating permissions without shedding the outdated ones; or perhaps, the initial access configurations might have been overly generous, driven by a different security perspective prevalent two decades ago. Furthermore, with the sheer number of users and the inevitable turnover over the years, keeping track of every user's exact role and correlating permissions can become an overwhelming task.
Use auditing tools and logs to determine which resources are genuinely being accessed by users. Extended inactivity can indicate outdated permissions.
Evaluate access frequency. If a user accesses a resource infrequently, they might not need constant access.
In large-scale security environments like ACF2, over time, the accumulation of outdated user profiles, rules, and permissions can contribute to a bloated security database, posing both manageability and potential security risks. Before transitioning to a role-based model, it's imperative to streamline and "clean up" these excesses. This is where the Cleanup utility from Broadcom becomes invaluable.
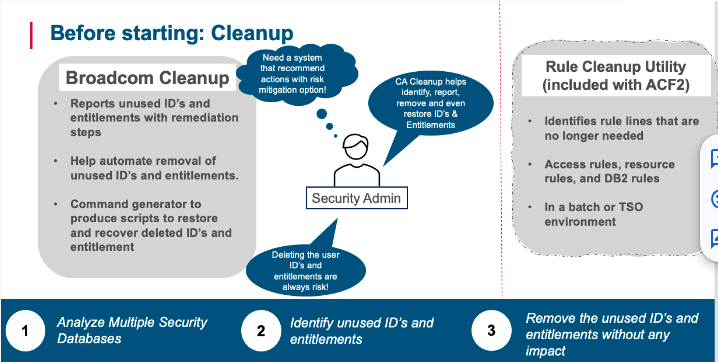
Broadcom Cleanup for ACF2 offers the following advantages:
Sites that choose to implement Cleanup for ACF2 would benefit from using the ACF2 Rule Cleanup Utility prior to loading the tracking database. Check out best practices for Cleanup here.
Before transitioning to a role-based access control model, having a streamlined and updated rule base is crucial. ACFRULCU aids in this by ensuring that only the most relevant and current rules are in play, making the role definition process more accurate and efficient.
The Rule Cleanup Utility (ACFRULCU) identifies rule lines that are no longer needed.
The lines can be from logonids or roles that no longer exist or UIDs that are no longer valid. You can also specify specific UIDs, logonids, or roles to remove from the targeted rules. You can use the utility for access rules, resource rules, and DB2 rules. The utility can be run against the active databases or alternate databases.
In essence, ACF2's Rule Cleanup Utility (ACFRULCU) offers a systematic and safe approach to refine and optimize rule databases. It not only enhances system performance but also lays down a cleaner framework for future security model transitions, such as adopting a role-based approach.
Stay tuned for my next post, which will continue this conversation by explaining the 5 steps for transitioning to Roles in your organization.
 Copyright © 2005-2025 Broadcom. All Rights Reserved. The term “Broadcom” refers to Broadcom Inc. and/or its subsidiaries.
Copyright © 2005-2025 Broadcom. All Rights Reserved. The term “Broadcom” refers to Broadcom Inc. and/or its subsidiaries.
Comments