Approximately 70% of corporate data resides on the mainframe and most of it in Db2 for z/OS. This corporate data consists of business critical data that often includes Personally Identifiable Information (PII data). While far less frequent than in the good old days, disasters may still happen, and Murphy’s law applies: if data can be lost, it eventually will. Regular recovery tests are essential to keeping your data safe and secure.
In addition, most people think that external threats (such as an external hacker trying to access corporate data) are the most common data security issues. In reality, various studies have shown that internal threats comprise 80% of all security threats. In other words, companies should protect their corporate data against their own employees.
There are numerous Data Compliance Regulations, such as HIPAA (US federal law), GDPR in Europe, or PIPEDA in Canada. These industry or geographical regulations demand corporations to treat with caution their most precious asset: data. For instance, GDPR states that a Recoverability breach may occur when it is not possible to prove that PII data can be restored in a “timely manner” :
The GDPR article 32.1.(c) reads: “the controller and the processor shall implement appropriate technical and organizational measures to ensure (...) the ability to restore the availability and access to personal data in a timely manner in the event of a physical or technical incident.”
External Regulations aside, to ensure business continuity in the unlikely event of a Recovery scenario, it is a very good idea to define a Recovery Time Objective (RTO) for your business critical data.
Depending on the type of corporate data you own, the type of business you are in, and the geography you do business with, the regulations you want to comply with will be different. And the definition of Personal Information to protect will be different!
As a typical example, the format of social security numbers is different from one country to another:
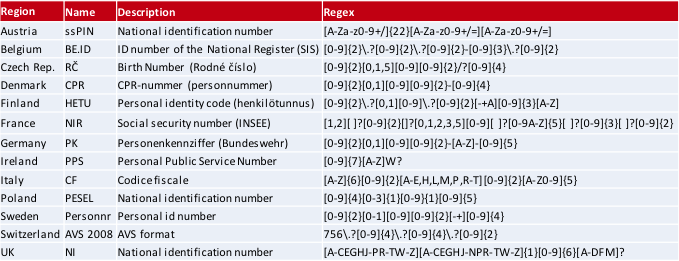
For instance, in the Czech Republic, the social security numbers (Rodné číslo) have a specific format, which is easier to describe using its Regular Expression (RegEx) format:
[0-9]{2}[0,1,5][0-9][0-9]{2}/?[0-9]{4}
Using a proper set of definitions for your business can help to determine the actual location of such data in your systems. The data most likely will reside in a set of dedicated databases, but to comply with Data Compliance Regulations, make sure sensitive data does not reside elsewhere, which can be a tremendous problem when not applying Data Gravity principles.
Locating business critical data is one thing, but ensuring it can be recovered in a timely manner is another. We recommend that you define Tiers of data, considering its sensitivity, along with business definition and guidelines for their respective Recovery Time Objectives.

This recommendation helps to provide unified guidelines for proper backup strategy and testing to the Operation team: Putting in place a backup strategy to comply with business Recovery Time Objectives is not a trivial task. Database Administrators have to balance the Recovery SLA expected by business leaders and customers with the system resources needed to back up the data.
Data Content Discovery lets you find and analyze the regulated and sensitive data on z Systems™ by scanning through various data sources such as IBM Db2, Datacom®, IDMS, IMS, and file types, including Physical sequential, PDS/PDSE, VSAM, and USS. Understanding who has access to regulated or sensitive data and encrypted status help mitigate the risks of potential audit findings, data breaches, and regulatory violations. The solution comes with several predefined classifiers to comply with various well-known regulations like GDPR, PCI, and PII specific to the country or industry. Tag rules allow you to streamline the selection of data sources, get reports specific to your Business application or department, and prepare for an audit.
Since most of the Mainframe corporate data resides in Db2 for z/OS, check out Db2 Recovery Suite, which includes Data Recoverability Compliance capabilities helping to validate that you have the necessary resources needed to perform a successful Db2 Recovery, and that you can do so in a reasonable timeframe. The Db2 Recovery Suite also includes the necessary tooling to plan for and execute, an efficient backup strategy.
 Copyright © 2005-2025 Broadcom. All Rights Reserved. The term “Broadcom” refers to Broadcom Inc. and/or its subsidiaries.
Copyright © 2005-2025 Broadcom. All Rights Reserved. The term “Broadcom” refers to Broadcom Inc. and/or its subsidiaries.
Comments